The Art of InfoSec
Written by adminNearly 2,500 years ago, in his seminal Art of War, Sun-Tzu quilled “Every battle is won before it is ever fought.” Although military-strategies remain somewhat timeless, tactics change- war is constantly evolving, from the outside flanks of Alexander the Great, to the hackers lurking on the Dark-Web today, no one is ever truly safe from collateral-damage, offline and now online. According to a study conducted by FICO, 61% of companies surveyed believe that the information-security (InfoSec) threat-environment will be worse next year– a rational fear, if the recent #wannacry ransomware-attack preludes any indication. Incredibly, only 51% of those respondents in the previously mentioned study maintain an executable disaster-recovery plan for lost-data or counter-measures in-place to neutralize exploits.
Every battle is won before it is ever fought. -Sun Tzu
As one of history’s greatest “Killer-Elite,” the ancient Samurai were hailed for attacking any and all opponents with tenacious ferocity, in spite of all odds. How did they achieve such an incredible state of mind? The answer is in the question: the Samurai mindset obsessively focused on the process of warfare- training with precision in-hand, not the outcome out of reach. Even as an army of one, the Samurai could inflict tremendous damage causing massive casualties; as individual-developers, we too can wield the Samurai-mindset by controlling the development-process to crush the hackers with our very own #ArtOfInfoSec.
Know Your Enemy
That’s what the FBI could never understand — that what Paulie and the organization does is offer protection for people who can’t go to the cops. The Mafia is like the police department for wiseguys. -Henry Hill, Goodfellas
Any fan of Spaghetti-Westerns knows that this genre is just a cheap knock-off of ancient Samurai legends and folklore revering honor and civility amidst imperial chaos. Hackers are the new mafia: digital mercenaries marauding the cyber-streets where enforcement is scarce, offering brute-force to the highest bidding nation-state, corporation or other criminal enterprise- because anyone who has ever dialed 911 to report a suspected hack at home or from a small-businesses has seen an officer’s 1000 yard-stare: simply stated, our country is ill-equipped to handle attacks at the local-level. As digital-frontiersman, we cannot depend on the arrival of a new sheriff in town quite yet; we must be self-reliant in the new Wild-West.
How to properly #InfoSec/#OpSec with @FiskarsAxes #demoed by our very own @theajsingleton…⛑ pic.twitter.com/OEsxXjzxbj
— BucephalusDev (@BucephalusDev) July 9, 2017
Renowned forefather and polymath Benjamin Franklin once said: “By failing to prepare, you are preparing to fail.” At BucephalusDev, “We are full-stack engineers trained in the art of business-” so we spare no expense in leading by example to deliver world-class web-presence, from the front-end to the back-end: we are covered by a standard “Errors and Omission” policy issued by our partners at Insureon to mitigate cyber-risk in the event of a compromise, as stated within our website Terms and Conditions section. Nearing our second anniversary of incorporation, we’re still stunned by the lack of cyber-insurance offerings marketed to small-businesses, which is roughly 46% of GDP. Dark Reading recently noted that cybersecurity-insurance is lacking at over 50% of companies; that is a staggering statistic considering almost every company is a “tech-company” nowadays.
BucephalusDev Certificate of Liability Insurance (Errors and Omission) by Insureon by Bucephalus Web Development on Scribd
The Art of InfoSec: BucephalusDev Bashito
When a web-application or website is ready for deployment, programming ends where DevOps begins, or as defined by Amazon Web Services: “the combination of cultural philosophies, practices, and tools that increases an organization’s ability to deliver applications and services at high velocity.” As a team of teams, BucephalusDev is Agile LEAN– so we only build state-of-the art web-applications with the most robust frameworks and technologies: we peer-pair on every production; we securely manage source-control with a remote Git-repository accessible only via two-factor authentication (2FA) and Secure SHell (SSH); we conduct unit-tests locally before deploying to production. The BucephalusDev Bashito (typo intended for pun:) is essentially our code to the Art of InfoSec, a sub-process detailed by the following:

Secure Password Management
The majority of hacks do not start on the command-line: they begin with social-engineering, or tricking a victim into revealing compromising information that is later exploited on-line against their will; repetitive-use of passwords derived from combinations of children’s birthdays or dog-names are simply no match for today’s script-kiddy. Security starts with the developer upon logging into the application tool-chain: randomly-generated, alphanumeric password manager applications, such as LastPass, are absolutely essential for not only secure password-management but also for encrypted file-exchange between clients and developers- even for notes and databases! Whatever the case may be, DO NOT SHARE PASSWORDS via text-message or e-mail because workstations are frequently unattended. Require clients to register and sign-up for a free LastPass account upon onboarding.
Pandora’s Inbox
From “The Fappening” to Wikileaks, we’ve clearly opened Pandora’s Inbox. OpSec includes behavioral conduct: don’t document, e-mail, message, photograph or text content that could potentially damage your business if publicly-leaked or, “doxed.” Mitigate doxing-risk by diversifying communication streams: reserve e-mail for important matters of record and external communications; for everyday internal communications, use a messaging-service like Slack, or preferably SpiderOak’s Sempahor. Ideally, files should be shared securely on the cloud using permission-handling via Google Drive, Dropbox or the equivalent- yet even that is not enough, especially in the wake of the recent GoogleDoc spear-phising attack ostensibly enveloped as a Google Document e-mail invitation but was nefariously attached with a worm spreading to all users stored in the infected-user’s address-book. Spoofing is the creation of email messages with a forged sender address; establish internal protocols and controls for personnel who may receive external communications.
Two-Factor Authentication
Enabling two-factor authentication (2FA) wherever possible is also advised- especially for mission-critical systems, such as Amazon Web Services, Bitbucket or Github repositories, and domain-management systems. If 2FA isn’t available via telephone, text or e-mail, the Authy and Google Authenticator smartphone applications reliably integrate with participating vendors connected via API.
Wild, Wild West
After conducting a keyword-research for the intents and purposes of SEO, one of the very first steps in web-development is purchasing a domain-name recorded by the Domain Name System (DNS). In actuality, every email and website address uniquely corresponds to a numeric IP-address (e.g. bucephalus.io => 192.124.249.18), which is propagated to the Internet Corporation for Assigned Names and Numbers (ICANN) directory- essentially the “Internet’s phonebook.” Upon reviewing [our company-domain](https://bucephalus.io) with a DNS-inspection application like MXtoolbox, the registered-agent contact-details are listed, intentionally in our case, as we’ve elected to reveal the appointed-agent and company-address filed under our company articles of incorporation in order to establish legitimacy and credibility with our prospective-clients, partners and obligors; however, it is generally inadvisable to register domain-names for personal-account details and addresses, such as a personal-residence. If unable to incorporate with a commercial address, Google-Domains and reputable hosting-providers like Namecheap offer privacy-options to conceal registered account-details affiliated with the domain for a nominal fee.
For hosting, we highly recommend Amazon Web Services (AWS) offerings for any micro/ec2 instances because they are so easily scalable for massive builds; in fact, our latest VETSI-production is hosted via Amazon Light Sail, which is essentially “AWS-lite” packaged with an Ubuntu 16.04 server capable of hosting a custom WordPress website. Upon deployment, DNS management is readily available via AWS Route 53 to dynamically re-task A-records- again, we prefer AWS because it features an array of offerings: a one-stop shop in web-development.
Let’s Encrypt
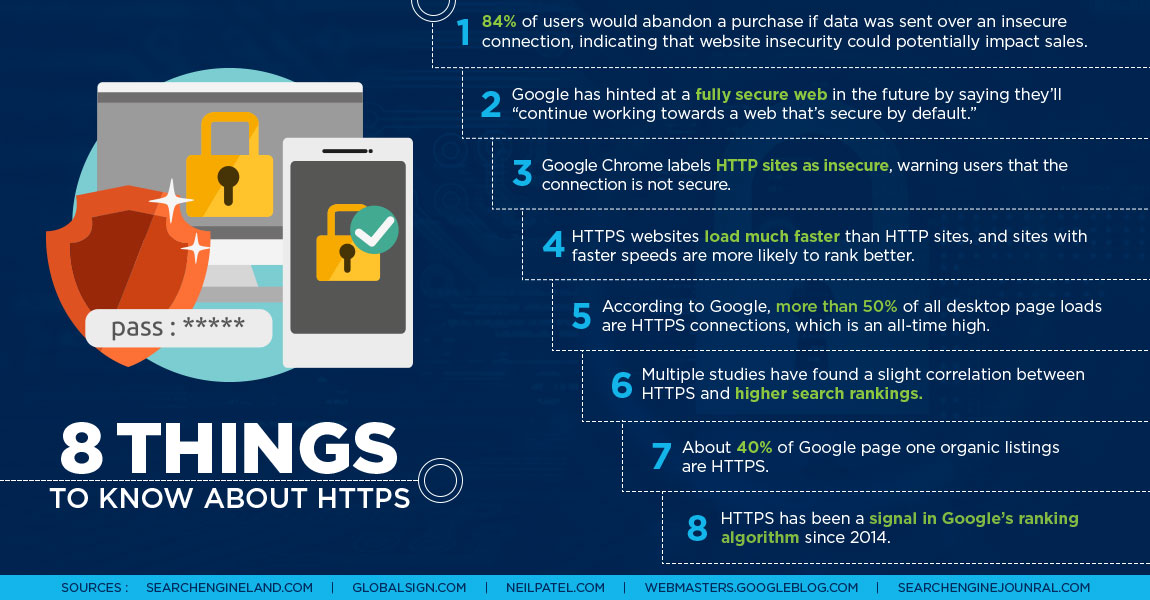
Why is HTTPS important? It guards against the middle-men trying to “listen-in” on your Internet-connection. Virtually every business and blog is accessible to the open-world by a universal-request link (URL), or “links” via the Hypertext Transfer Protocol (HTTP) which, without SSL (secure-socket layer) (HTTPS) may be a problem, especially if using web-application featured on website that is susceptible to fuzzing: or the automated process of finding hackable software bugs by randomly feeding different permutations of data into a target program until a vulnerability is discovered and exploited. A website connection established via HTTPS initializes a key reconciled to a cryptographic hash-function privately-paired to another key-value. When installed on a web server, HTTPS-validation is signified by the padlock-icon prefixed to the browser address-bar. Although only less than 1% of all websites are secure, 40% of Google’s page one organic search results feature an HTTPS site. Google has encouraged webmasters to make the migration to a secure site for a while now and has been giving an increasing amount of weight in ranking boosts to websites that are HTTPS, officially noting: “As migrating to HTTPS becomes even easier, we’ll continue working towards a web that’s secure by default. Don’t hesitate to start planning your HTTPS migration today!”
Before the The Let’s Encrypt movement, SSL-certification required some DevOps skills, but now most hosting-providers like Namecheap offer turn-key solutions for HTTPS certification; in fact, The LetsEncrypt movement, in cooperation with the Electronic Frontier Foundation (EFF) created CertBot: a one-liner passed via the command-line for nice and easy implementation on various hosting-environments, like standard Apache-platforms for Ubuntu-servers provided within the markdown below:
$ sudo certbot --apache
A Great Firewall
The largest hack to date was a denial of service attack DDoS targeting the Dyn Corporation, a company that controls much of the Internet’s domain name system (DNS) infrastructure in conjunction with the previously mentioned ICANN. On 10/21/16, a network of computers infected with special malware, known as a “botnet” distributed a coordinated payload of fake user-traffic, or “bots,” exhausting Dyn-servers to shut-down, disconnecting most of the known Web that morning from Twitter, Netflix, Reddit, CNN and many other websites in Europe and the US. Think of that annoying flash of light reflecting from a wrist-watch nearby- that’s a proxy-server bouncing the original light-source, or rather content, to your browser-purview. A proxy-server service provider like Sucuri is designed to deflect DDoS attacks by redirecting the web-server source-code to another server hosting as a “reverse-proxy,” by intercepting and inspecting all incoming HTTP/HTTPS requests to the website then stripping them of any malicious requests before the they arrive safely at your server. A proxy-server also affords optionality to authorize designated IP-addresses for access to server-side administration panels and content management systems. Furthermore, in the event of DDoS attack the proxy-server can be re-tasked to another server from the original source-code.

Overkill: Always Have a Plan B, C & D
Many hosting-providers routinely take snapshots of server-side instances on a weekly basis, so the hosting-provider is one ping away from a rollback to the week-prior but web development agencies should devise additional contingencies- consider the following scenario: a small-business depends on a custom-WordPress production for not only client-side point-of-sale (PoS) for fitness-classes and fitness gear store, but also scheduling systems via application program interface (API); however, a year later, that small-business became at the mercy of an acquisition stripping the hosting-provider’s world-class customer-service and support in exchange for prioritizing cost-savings and profitability; they decide to conduct emergency server-side maintenance without any warning whatsoever, which renders the subject small-business website in addition to all instances on the shared-server offline for the next 24 hours- the aforementioned is a true story that happened last year. Unfortunately, that small-business website was down for nearly 24 hours – not because of a hack or “cowboy-coding,” but because of a greedy hosting-provider; the BucephalusDev-difference builds for the worst case scenario: we hedge our cyber-risk by integrating robust API’s which can redirect users to multiple touch-points if a production sustains unexpected maintenance or attack. Moreover, every BucephalusDev production is guaranteed by a comprehensive disaster recovery plan restoring any website within 30 minutes of compromise; we archive daily snapshots and test rollbacks on a staging-server for a temporary redirect with BlogVault, which is essentially a RollBack-as-a-Service, providing daily automatic backup and synchronization of every aspect of the web-stack- from comments, media file, themes, plugins across multiple secure and robust servers, which are both encrypted on their servers, and with Amazon S3 redundancies.
Build your Opponent A Golden Bridge
To secure peace is to prepare for war. -Karl von Clausewitz
The Air Force Parajumpers are admired for selflessly deploying into the most treacherous battlefields and hot-zones to rescue downed airmen and soldiers behind enemy lines – even our beloved astronauts – “So others may live;” but make no mistake – these heroes are the most highly-skilled killers as “Jacks of all Trades,” a title earned after graduating “Superman School,” or two years of intensive-training with one of the highest attrition-rates in the entire U.S. Special Operations Forces- almost 80%. Full-stack web-developers are the Internet’s PJ’s: we creatively build and collaborate as the World-Wide-Web’s “Jacks of All Trades,” so we must know the art of information-security in order to protect our clients from the hackers lurking on the darkest corners of the Internet. Karl von Clausewitz, another godfather of war later penned, “To secure peace is to prepare for war-” and so let us end with the BucephalusDev #ArtOfInfoSec to not only secure for peaceful web development, but remain prepared for the ever-evolving war waged on multiple-fronts by today’s cyber-warriors: developers, engineers, hackers and even search-engine-marketers (SEM), because at the end of the day, search-engine optimization (SEO) is nothing short of best-practices in web-development– from the front-end, all the way to the back-end.

Categories: InfoSec